This post describes how to handle AS2Go to run the attack!Assuming you finished the attack preparation.
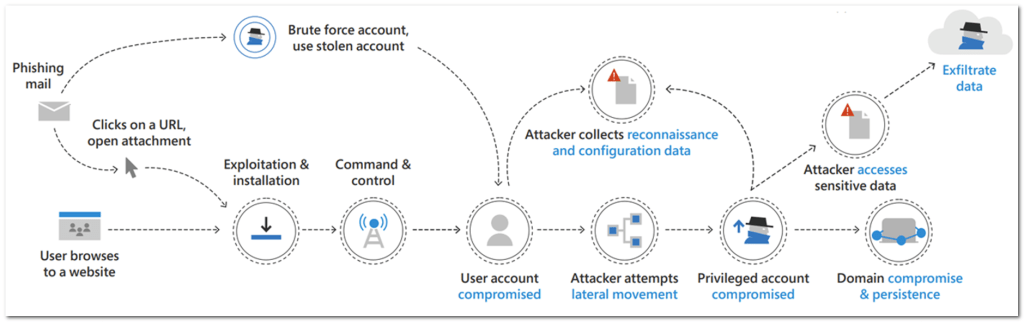
The attack runs step-by-step alone the cyber kill-chain and covers the following attack stages:
Continue readingThis post describes how to handle AS2Go to run the attack!Assuming you finished the attack preparation.

The attack runs step-by-step alone the cyber kill-chain and covers the following attack stages:
Continue readingThis post describes how to prepare the lab before you run the attack!Assuming you finished the configuration on DC, AdminPC & VictimPC.
This post describes how to prepare the Admin PC for the attack scenario, to simulate domain activities from Admin PC.Assuming you already finished lab setup 1/3 and setup an Active Directory join workstation (English OS) you have to do the following steps on your Admin PC.
In this post I describe how to configure a Hyper-V virtual network switch into promiscuous mode. This mode allows you to monitor external traffic, eg. Needed for Microsoft Defender for IoT.Assuming you already created an dedicated virtual network switch, you have to run these four steps.
Welcome to my blog,
which will cover topics around Microsoft 365 & Azure Security!