I hold this session during the HIP Europe 2021 in June 2021.
Summary
Learn how to identify and investigate Lateral Movement and how to de-risk LMPs using Microsoft Defender for Identity.
Notes
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
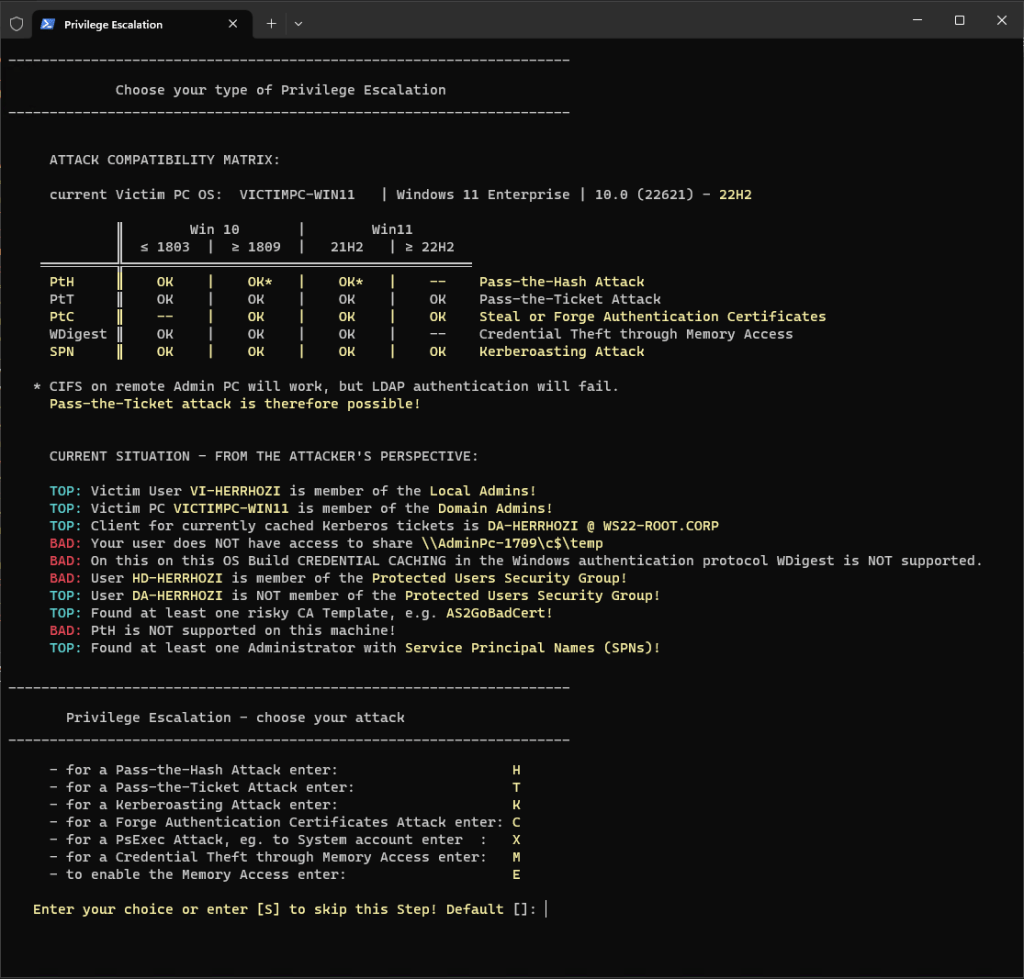
Learn a “life hack” (brute-force attack a overpass-the-hash attack a pass-the-ticket a domain dominance) and how to identify and investigate Lateral Movement and how to de-risk LMPs using Microsoft Defender for Identity.
Here you find my recording, which shows AS2Go v1.x.