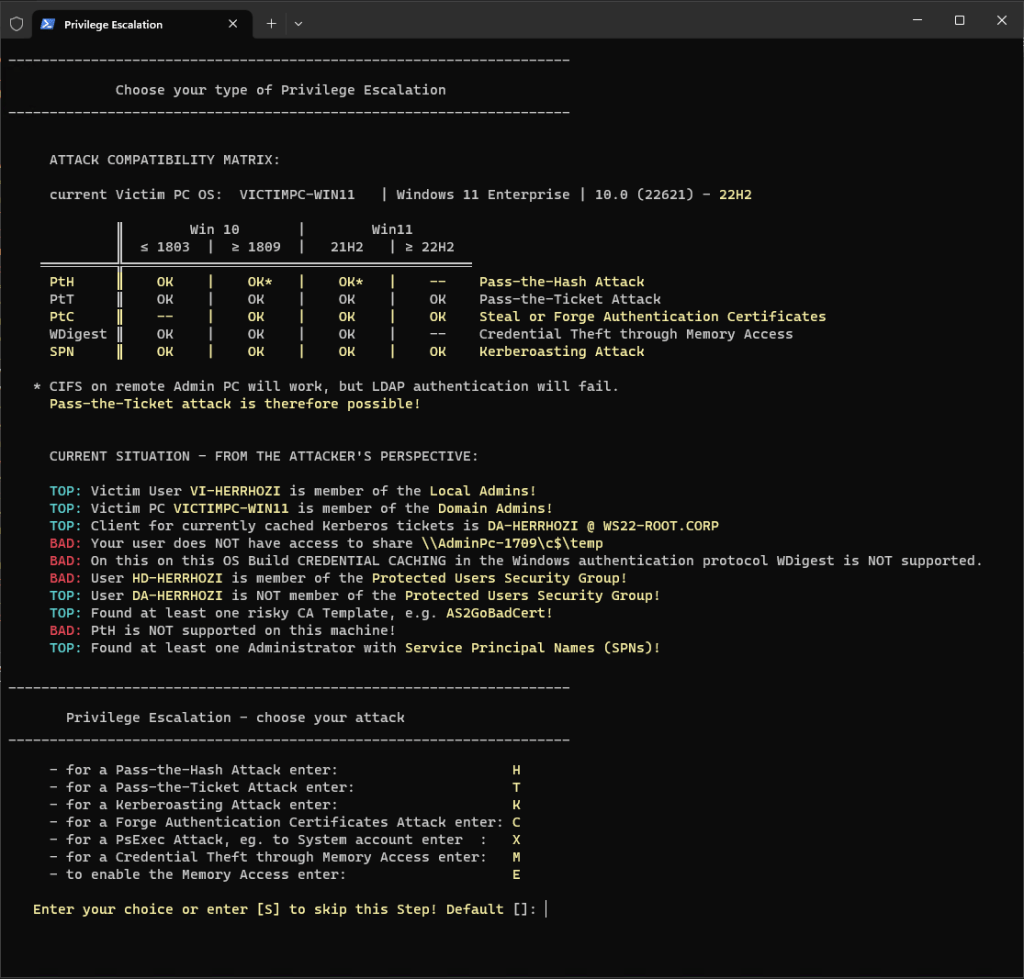
Find the best attack based on Victim’s PC Operation System (OS Build) and the current situation
Which, among other things, is taken into account?
- Is the Victim a local admin on the Victim PC?
- Is the Victim PC member of the Domain Admins or Account Operators?
- Client for currently cached Kerberos tickets?
- Does this Client/User have access to c$ share on Admin PC?
- Is the Windows authentication protocol WDigest supported?
- Is Pass-the-Hash Attack supported?
- Is the Helpdesk User & Domain Admin member of the Protected Users Security Group?
- Is Forge Authentication Certificates Attack supported?
- Is a risky CA Template available?
- Found at least one administrative account with Service Principal Names (SPNs)?
CURRENT SITUATION – FROM THE ATTACKER’S PERSPECTIVE:
.
2 thoughts on “Choose your type of Privilege Escalation”