AS2Go is an acronym for Attack Scenario To Go.
AS2Go is written in PowerShell and goes along the cyber kill chain, with stops at Password Spray, Reconnaissance, Privilege Escalation, Sensitive Data Access & Exfiltration and Domain Compromise.The GIF shows a typical attack along the kill-chain. Starting with stolen credentials and ending with a compromised domain.

The basic idea of AS2Go
My goal is to create expressive and representative Microsoft Defender for Endpoint ⬈ & Identity ⬈ alerts or rather Microsoft 365 Defender ⬈ & Microsoft Sentinel ⬈ incidents.
Within my current role in the Semperis Breach Preparedness and Response team, an additional goal of AS2Go is to increase awareness of how easy it is to abuse a vulnerability or misconfiguration to compromise the entire Active Directory.
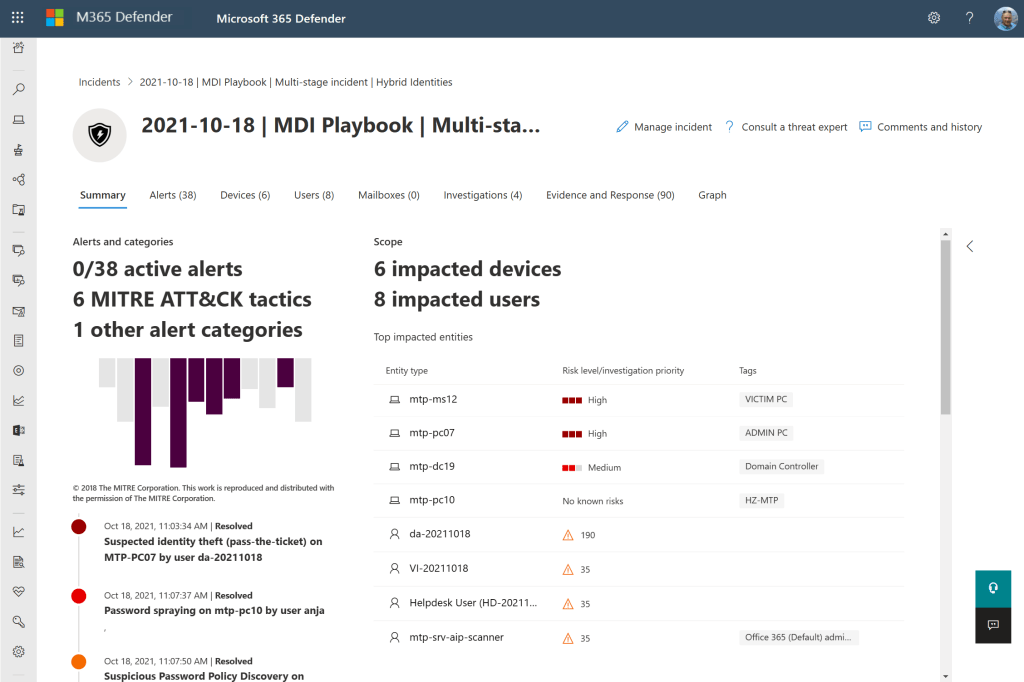
See how the PoSH script works
I used the Microsoft Defender for Identity playbook ⬈ as template for my script.
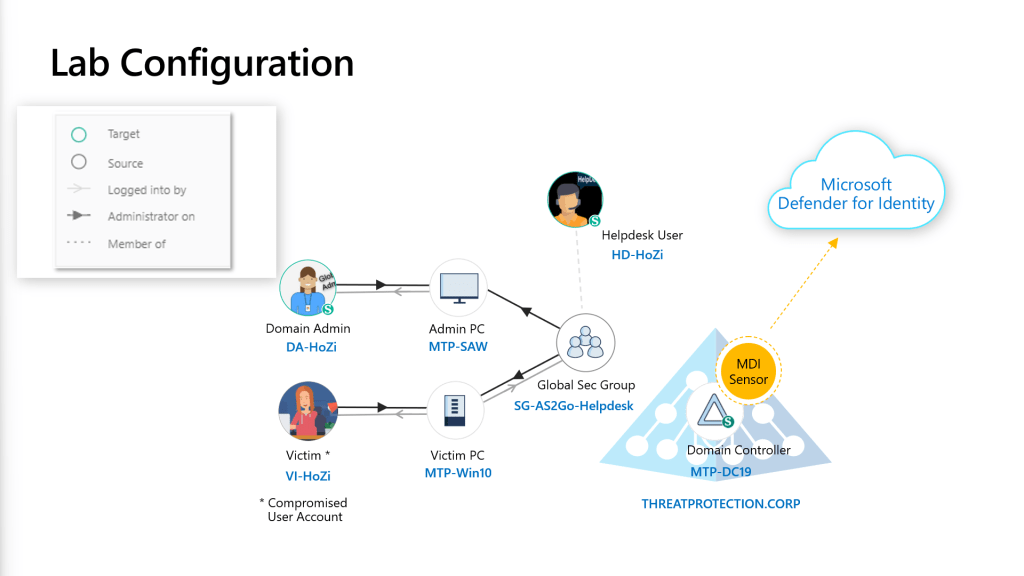
My Lab Architecture & Configuration
In this lab, there are three (3) main servers & computers.
- Domain Controller
- Admin PC
- Victim PC
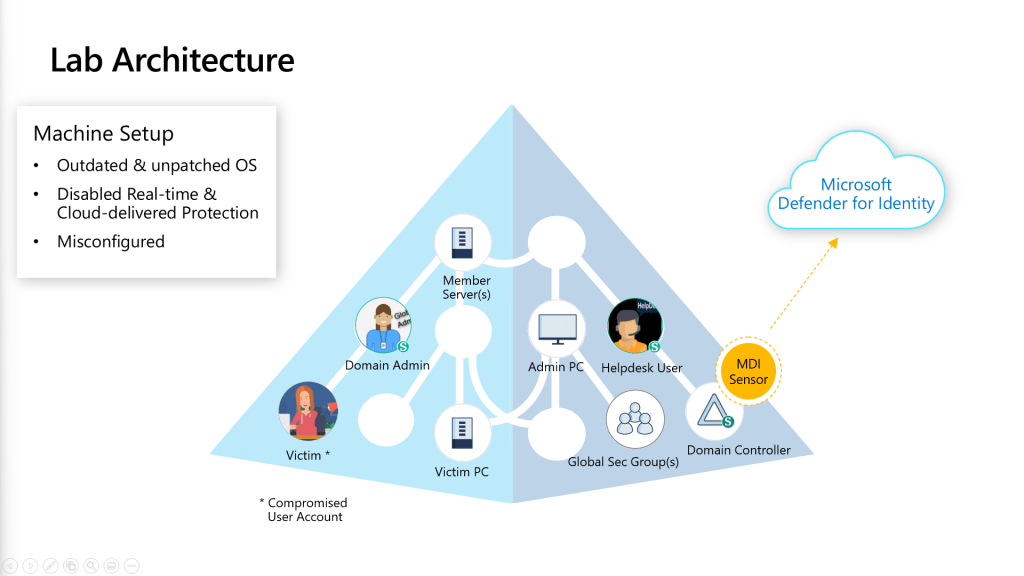
and there are three (3) main users.
- DA-xxxxx | Domain Admin
- HD-xxxxx | Helpdesk User
- VI-xxxxxx | Victim (Compromised User)
Possible Lab Setups
I tested the attack scenario against several lab setups, see more details here:
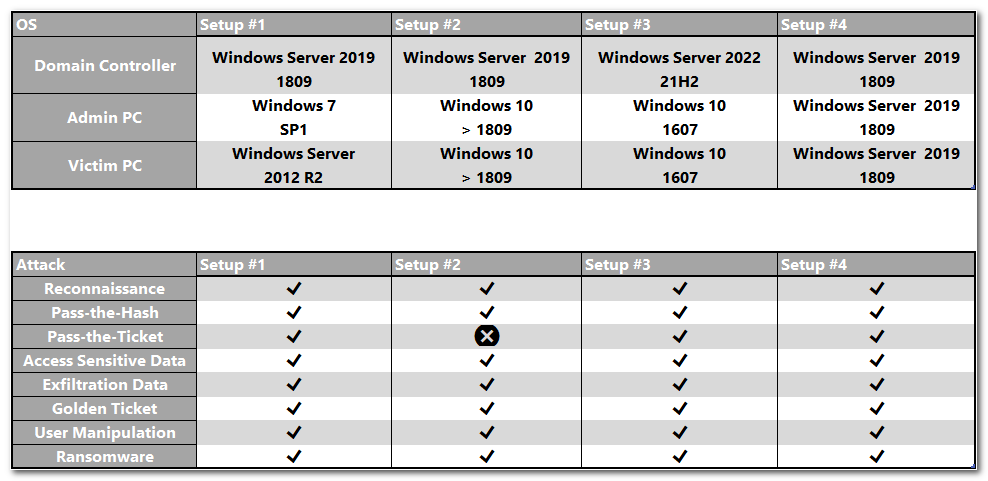
While using Mimikatz.exe Version 2.2.0-20210810-2 | Aug 10 2021 17:19:53Check out my Lab Setup instructions
- AS2Go – Lab Setup instructions
- AS2Go – Prepare the Attack ⬈
- AS2Go – Run the Attack ⬈
I recommend following the lab setup instructions as closely as possible.